The Lewis Framework for IT and CyberSecurity Transformation
Created by Elliot Lewis, the Lewis Framework allows entities to use our Core Principles to focus on transformational strategies, alignments and design for the advancement of your operations and cyber-security.
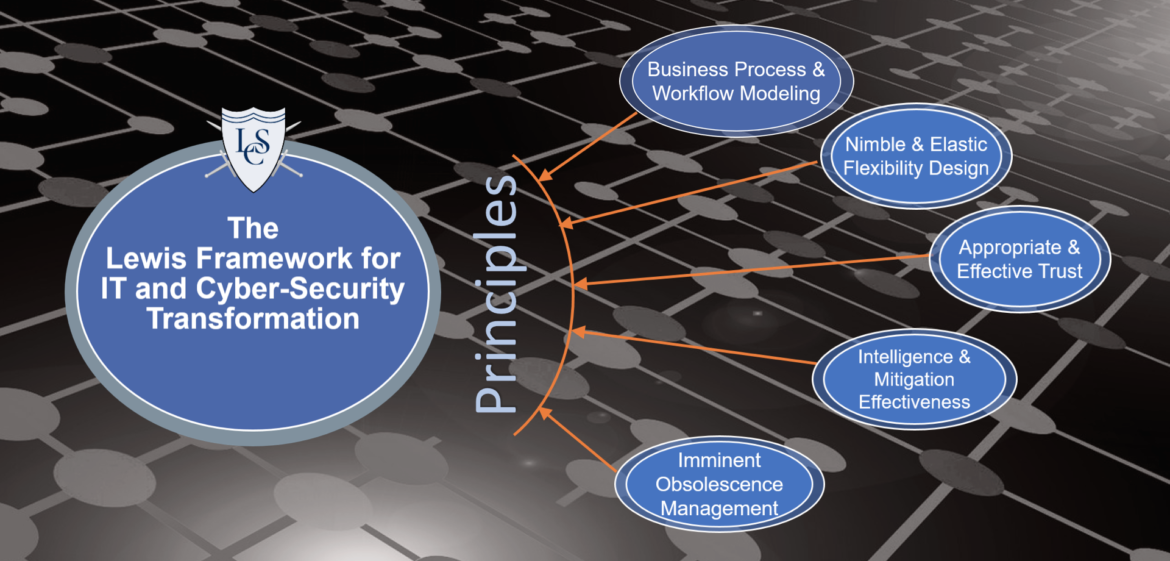
Many of our client engagements start with focusing on a particular problem, issue, or initiative within IT and Cyber-Security operations- and that is always a good way to start! The Framework allows us to look at all angles when considering any given problem. It allows us to be specific and - at the same time - holistic and comprehensive.
By utilizing the Lewis Framework, we can comprehensively focus on making sure that:
- The DNA of the business is the root of the solution. Instead of working off of "industry models" or regulatory checklist - we focus on how the business operates, how it generates revenue, competes within its target markets, and utilizes its data to drive ecosystem enablement.
- Businesses grow, expand, and adjust to their market demands and their customer base. In order to do so, they need to assess, adopt and deploy new technologies at a near-constant rate to stay competitive. As technology evolves, so must the security mitigations that protect that technology. No threat model remains static over time. Nimble Flexibility is core facet of any proper design.
- Businesses need to be able to trust their systems, their dataflows, and their users - all of which combine into the workflows that define and enable a business to succeed. Trust is more than just an identity - it's about understanding your ecosystem, your services, your users and customers - and how your data is flowing, where it is flowing to, why, and when. Identity and Access Management solutions need to be defined, designed and deployed in a way that flexible, articulate and versatile - yet secure and resilient. A rigid IAM design will lead to blockages, where a "loosely coupled and flexible" design will lead to nimbleness and competitive advantage.
- No business is static - so no technology architecture or corresponding threat model is static either. "Snap-shot" security assessment lead to a false sense of security - and that can lead to openings for threat actors to take advantage. When true intelligence ops are developed, we can see when security solutions start to lose - or will being to lose - the effectiveness as the business evolves. Understanding Threat Intelligence Ops, Mitigation Effectiveness Modeling, and Imminent Obsolescence Awareness will allow the business to be able to grow and compete - all while minimizing operational and cyber risk.
The Lewis Framework and its Core Principles will ensure that technology operations will operate with peak capabilities and security.